华为防火墙配置NAT转换

华为防火墙配置NAT地址转换
本实验使用ensp仿真模拟器配置
实验目的
配置HFW1防火墙各种地址NAT地址转换
实验设备
华为USG6000v一台(简称FW1)
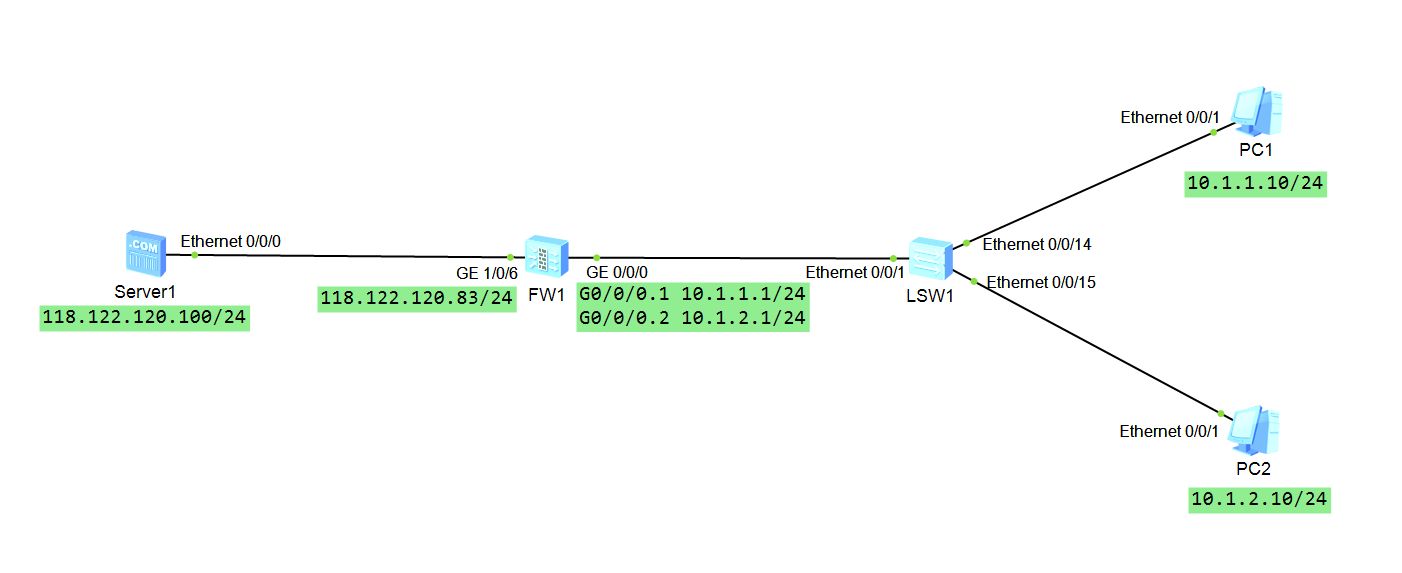
实验拓扑
基础配置
- 改名,改密码,关闭信息中心。
1
2
3
4
5
6
7<USG6000V1>sy
Enter system view, return user view with Ctrl+Z.
[USG6000V1]sy FW1
[FW1]un in en
Info: Saving log files...
Info: Information center is disabled.
[FW1] - 配置IP地址
1
2
3
4
5
6
7
8
9
10
11
12
13[FW1]int g1/0/6
[FW1-GigabitEthernet1/0/6]ip add 118.122.120.83 24
[FW1-GigabitEthernet1/0/6]q
[FW1]int g0/0/0.1
[FW1-GigabitEthernet0/0/0.1]ip add 10.1.1.1 24
[FW1-GigabitEthernet0/0/0.1]vlan-type dot1q 10 #封装vlanid
[FW1-GigabitEthernet0/0/0.1]service-manage ping permit
[FW1-GigabitEthernet0/0/0.1]q
[FW1-GigabitEthernet0/0/0.2]ip add 10.1.2.1 24
[FW1-GigabitEthernet0/0/0.2]vlan-type dot1q 20 #封装vlanid
[FW1-GigabitEthernet0/0/0.2]service-manage ping permit
[FW1-GigabitEthernet0/0/0.2]q
[FW1] - 配置安全区域
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21[FW1]firewall zone untrust
[FW1-zone-untrust]add int g1/0/6
...
[FW1]firewall zone trust
[FW1-zone-trust]add int g0/0/0.1
[FW1-zone-trust]add int g0/0/0.2
...
#
trust
priority is 85
interface of the zone is (3):
GigabitEthernet0/0/0
GigabitEthernet0/0/0.1
GigabitEthernet0/0/0.2
#
untrust
priority is 5
interface of the zone is (1):
GigabitEthernet1/0/6
# - 配置安全策略
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15[FW1]security-policy
[FW1-policy-security]rule name to_untrust
[FW1-policy-security-rule-to_untrust]source-zone trust
[FW1-policy-security-rule-to_untrust]destination-zone untrust
[FW1-policy-security-rule-to_untrust]source-zone local
[FW1-policy-security-rule-to_untrust]action permit
...
#
security-policy
rule name to_untrust
source-zone local
source-zone trust
destination-zone untrust
action permit
# - 配置交换机vlan
1
2
3
4
5
6
7
8
9
10
11
12
13
14vlan batch 10 20
#
interface Ethernet0/0/14
port link-type access
port default vlan 10
#
interface Ethernet0/0/15
port link-type access
port default vlan 20
#
interface Ethernet0/0/1
port link-type trunk
port trunk allow-pass vlan 2 to 4094
#
Easy-ip转换
Easy ip——允许将多个内部地址映射到网关出接口地址上的不同端口
配置nat策略:
1 | [FW1]nat-policy |
测试结果
PC1(vlan10 IP地址:10.1.1.10) ping server1(118.122.120.100)
1 | PC>ping 118.122.120.100 |
将trust地址转换为防火墙出口地址,端口不同
1 | [FW1]dis firewall session table |
PC2(vlan20 IP地址:10.1.2.10) ping server1(118.122.120.100)
查看会话表:
1 | Current Total Sessions : 5 |
IP转换为路由器的出口IP(118.122.120.83)
NAPT地址转换
NAPT: Network Address Port Transfer 网络地址端口转换。也叫PAT。
使用一个合法公网地址,以不同的协议端口号与不同的内部地址相对应,也就是<内部地址+内部端口>与<外部地址+外部端口>之间的转换
- 配置NAT地址池:2.配置nat策略
1
2
3
4
5
6
7
8
9[FW1]nat address-group napt_ip
[FW1-address-group-napt_ip]section 118.122.120.115 118.122.120.116
[FW1-address-group-napt_ip]mode pat
[FW1-address-group-napt_ip]dis this
...
nat address-group napt_ip 0 #地址池id
mode pat #pat模式
section 0 118.122.120.115 118.122.120.116 #地址池范围112.122.120.115~116
#1
2
3
4
5
6
7
8
9
10
11
12[FW1]nat-policy
[FW1-policy-nat]rule name napt
[FW1-policy-nat-rule-napt]destination-zone untrust
[FW1-policy-nat-rule-napt]source-zone trust
[FW1-policy-nat-rule-napt]action source-nat address-group napt_ip
[FW1-policy-nat-rule-napt]dis this
···
rule name napt
source-zone trust
destination-zone untrust
action source-nat address-group napt_ip
#
测试结果
PC1(vlan10 IP地址:10.1.1.10) ping server1(118.122.120.100)
1 | PC>ping 118.122.120.100 |
转换为地址池指定的IP地址:
1 | Current Total Sessions : 5 |
pc2省略
NO-PAT地址转换
NAT No-PAT是一种NAT转换时只转换地址,不转换端口,实现私网地址到公网地址一对一的地址转换方式。
1.配置NAT地址池
1 | [FW1]nat address-group no_pat_ip |
2.配置nat策略
1 | [FW1]nat-p |
Info: The current source conversion address pool type is no-pat, and if some businesses of the same user do not need to do NAT, please create a new rule with NAT type No-nat, otherwise the user’s business will be NAT.
提示:当前源转换地址池类型为 no-pat,如果同一用户的某些业务不需要做 NAT,请新建 NAT 类型为 No-nat 的规则,否则该用户的业务将为 NAT。
测试结果
PC1(vlan10 IP地址:10.1.1.10) ping server1(118.122.120.100)
会话表:
1 | Current Total Sessions : 5 |
结果:只转换ip地址,不转换端口。
- 标题: 华为防火墙配置NAT转换
- 作者: Clevebitr
- 创建于 : 2024-09-28 09:37:19
- 更新于 : 2025-04-18 22:06:47
- 链接: https://blog.clevebitr.dpdns.org/2024/09/28/华为防火墙配置NAT转换/
- 版权声明: 本文章采用 CC BY-NC-SA 4.0 进行许可。
